Hello, using Nmap with the -sV option, I found several vulnerabilities. In this post, I am going to exploit Samba SMBD.

As seen in the picture above, I don’t know the exact version of Samba; it ranges between 3.x and 4.x. Fortunately, there are other scanners besides Nmap. I started the Metasploit Framework and searched for 'auxiliary/scanner/smb'. There, I found a scanner that could help me determine the exact version of Samba. It's also interesting to note that I found the name of a workgroup, which might help me find another way to access this target in the worst case.
With the show info command, I first read through the description.
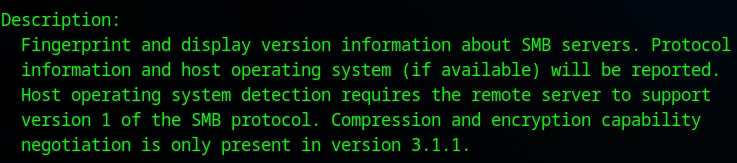
Next, I set up the scanner and start it.
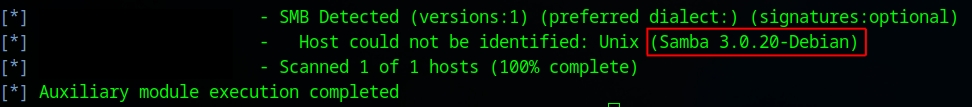
Even though the scanner indicated that it could not identify the host, it was still able to determine the version, which is Samba 3.0.20-Debian. With this information, I searched again through the Metasploit Framework and found only one result, which has an excellent rating.
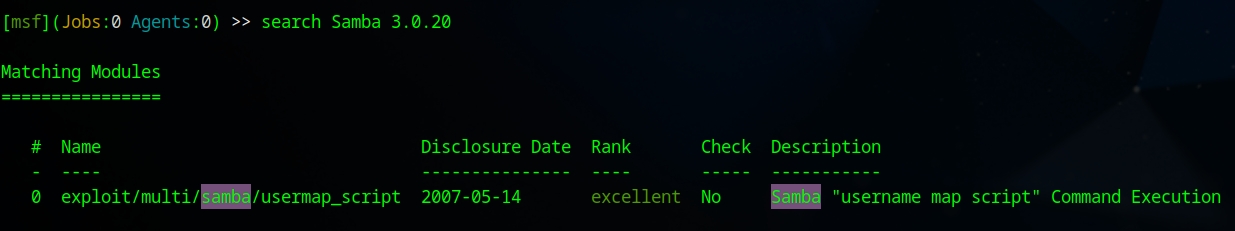
Additionally, the description is a perfect match for the version of Samba our target is using.
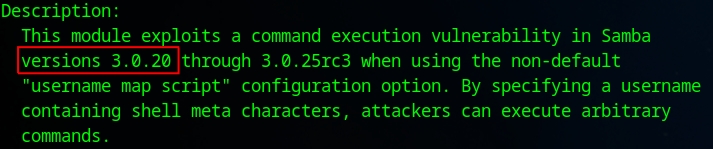
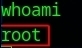
After setting everything up, such as the Rhost and payload, I ran it and got an open shell. As before, I can confirm that I gained root access.