

Hello, using Nmap with the -sV option, I found several vulnerabilities. In this post, I am going to explore another misconfiguration using Telnet as an example.
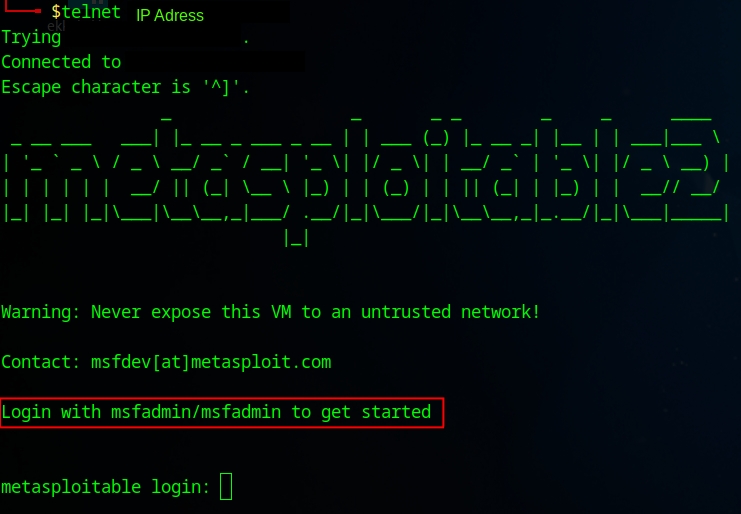
Connecting to Telnet is quite simple using the command 'telnet' followed by the IP address. In this example, the username and password are exposed. However, a common misconfiguration involves failing to change the default username and/or password, which allows logging into Telnet with usernames such as admin, anonymous, or root. Another example can be found in this post.
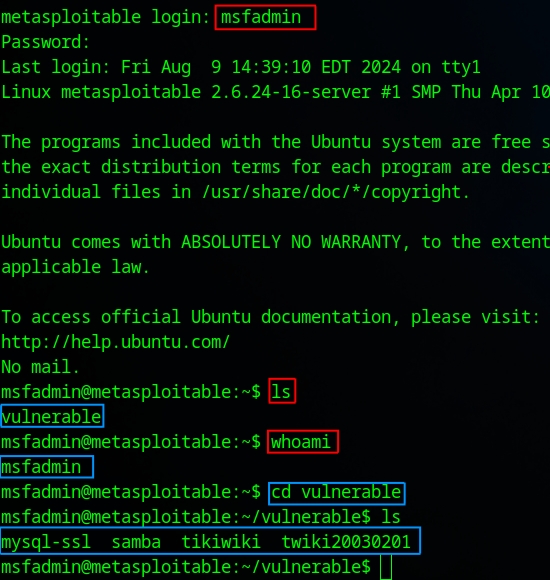
As seen in the image above, I was able to access the target via Telnet as the msfadmin user. I immediately found an interesting directory named vulnerable, which contains some vulnerabilities that I will cover in another post.