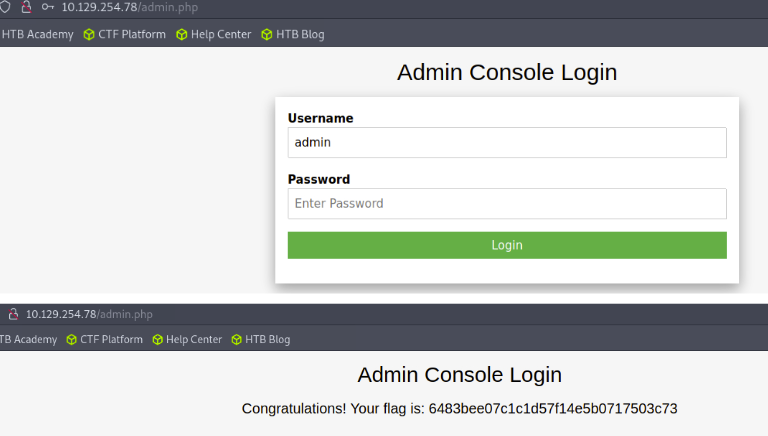
I began with an nmap version scan and found only one open port, which is port 80 running nginx version 1.14.2.
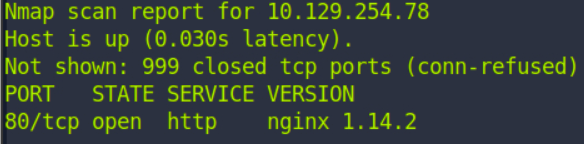
I opened the website to check if there are any obvious vulnerabilities.
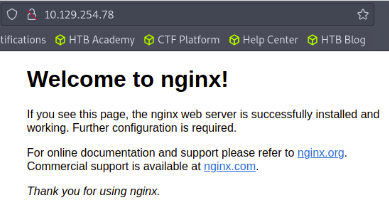
Before looking into the source code, I ran dirb and instantly found a very interesting subdomain.
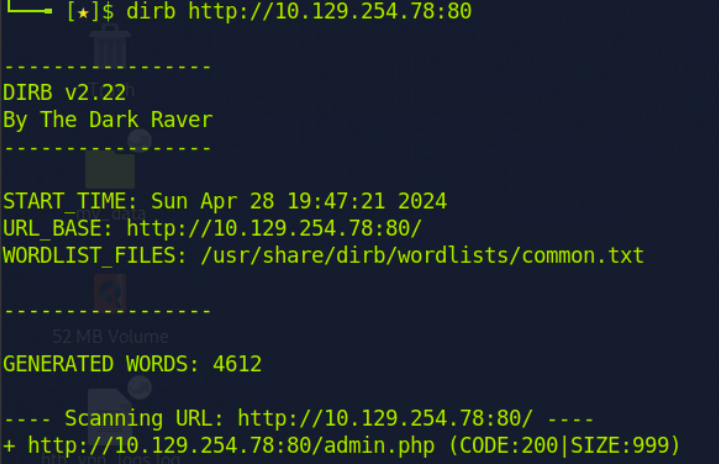
I opened the subdomain '/admin.php' and my first attempt with a misconfigured username and password was successful using 'Admin' as the username and 'admin' as the password.