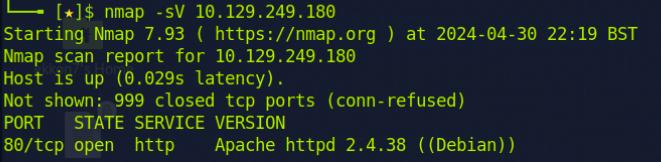
I began by conducting an nmap version scan and found Port 80 open.
I then opened Firefox and navigated to the website associated with this IP address. The site revealed a login page requiring a password.
Next, I opened a new terminal tab and ran Dirb to search for potential directories.
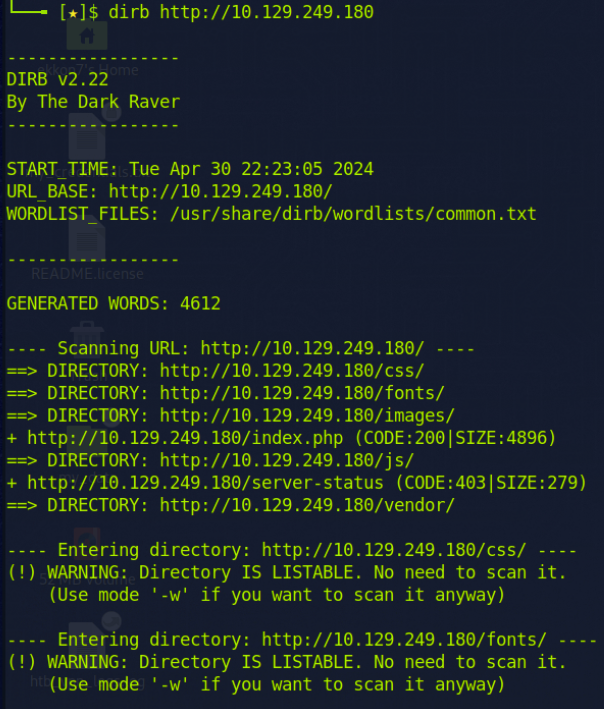
I looked inside the JS file and also opened the '/image/' directory but didn't find any useful information. The JS file was not minified or obfuscated in any way.
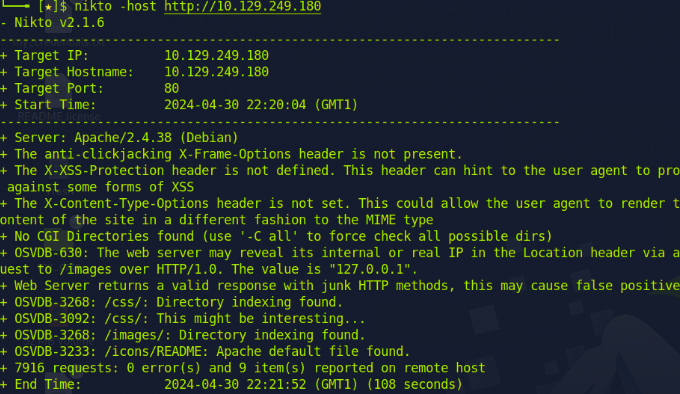
In another tab, I launched Nikto to identify any outdated versions used by the website.
Additionally, I initiated Gobuster in a separate tab to search for and potentially brute-force directories using the common.txt, big.txt and indexes.txt files from Dirb. I navigated to '/usr/share/dirb/wordlists' to try different txt files.
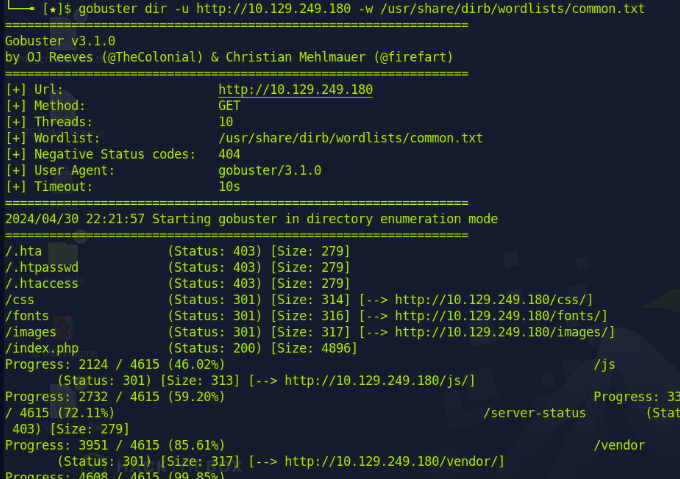
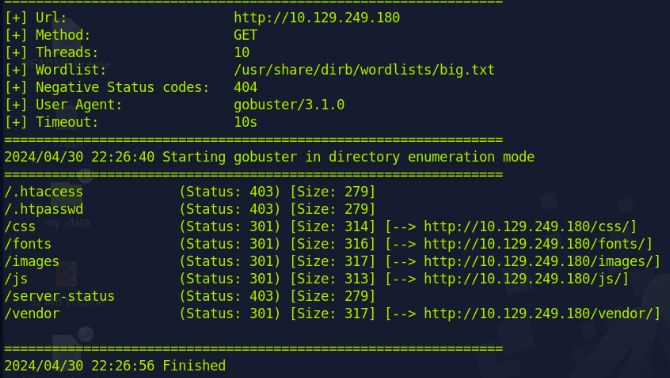
The 'common.txt' file, when used with gobuster, actually resulted in 1 directory fewer than when using dirb. The directory 'vendor' could only be found by gobuster using the 'big.txt' wordlist.
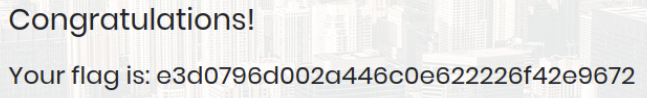
Since I could not find anything useful in any directory or in the JS files, I attempted some common misconfigured usernames and passwords such as admin:admin, guest:guest, user:user, root:root, and administrator:password. While testing those usernames and passwords, I also attempted to use special characters for a possible injection, and it appears that special characters are indeed allowed. That's why I attempt using the username admin'#. Adding the hashtag will comment out the rest of the query, rendering the search for a matching password for the specified username unnecessary. The script will now only check if any entry exists with the username 'admin'. Fortunately, I was successful in this case. There is indeed an account named 'admin', validating our SQL Injection.